A recent report from MobileSyrup revealed a staggering alleged data breach impacting over 89 million Steam accounts. The breach, tied to a third-party service, Twilio, used for SMS-based two-factor authentication (2FA), exposed sensitive data, including real-time 2FA codes, which hackers are now selling on the dark web for $5,000.
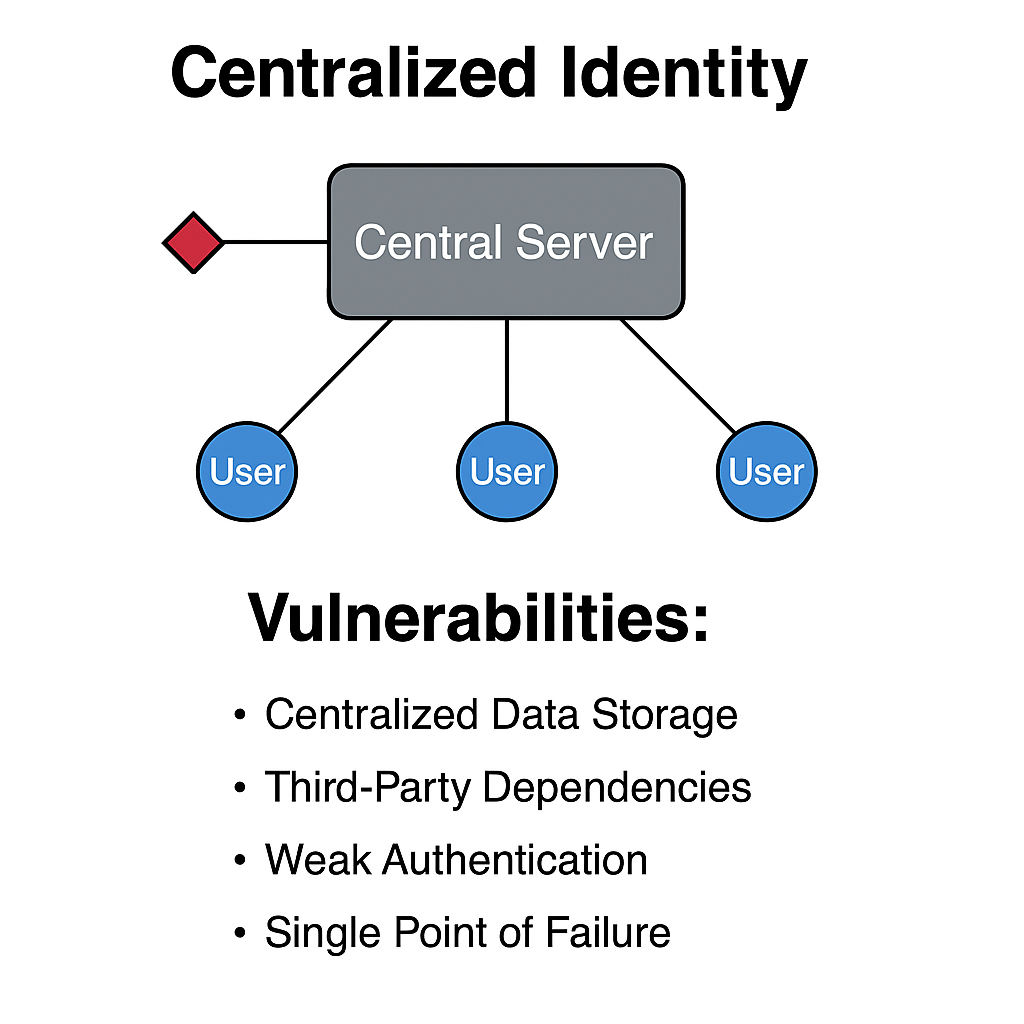
This incident, stemming from a supply-chain compromise rather than a direct attack on Steam, underscores a critical vulnerability in centralized identity systems. As gaming platforms like Steam manage millions of user accounts, the need for robust, secure identity solutions has never been clearer. Enter decentralized identity (DID)—an approach and tech stack that can protect users and platforms alike. In this article, we’ll explore why DID is the future of secure gaming, spotlight ArcBlock as a leading vendor, and provide a clear action plan for implementation.
The Problem: Centralized Identity Risks#
The alleged Steam breach underscores the inherent risks associated with centralized identity systems. Key vulnerabilities include:
- Centralized Data Storage: Centralized databases, used by platforms and their third-party providers, represent a single point of failure that can be targeted and exploited by attackers.
- Third-Party Dependencies: Relying on external services for critical functions like SMS-based 2FA introduces supply-chain risks. The security posture of the third party directly impacts the security of the main platform.
- Weak Authentication Methods: Methods like SMS-based 2FA are susceptible to interception techniques such as SIM swapping, allowing attackers to potentially gain access to one-time codes and compromise accounts.
The outcome of such vulnerabilities can be the exposure of sensitive user data, risking identity theft, financial loss, and privacy violations. Centralized systems, despite their convenience, present attractive targets for cybercriminals, and the gaming industry, with its vast user base, faces significant challenges in mitigating these risks.
Why Decentralized Identity is the Solution#
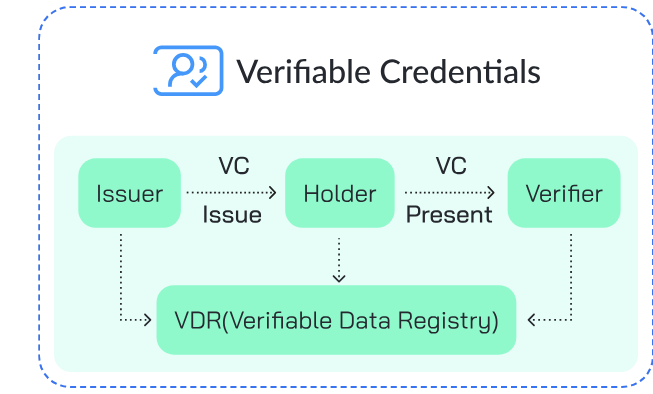
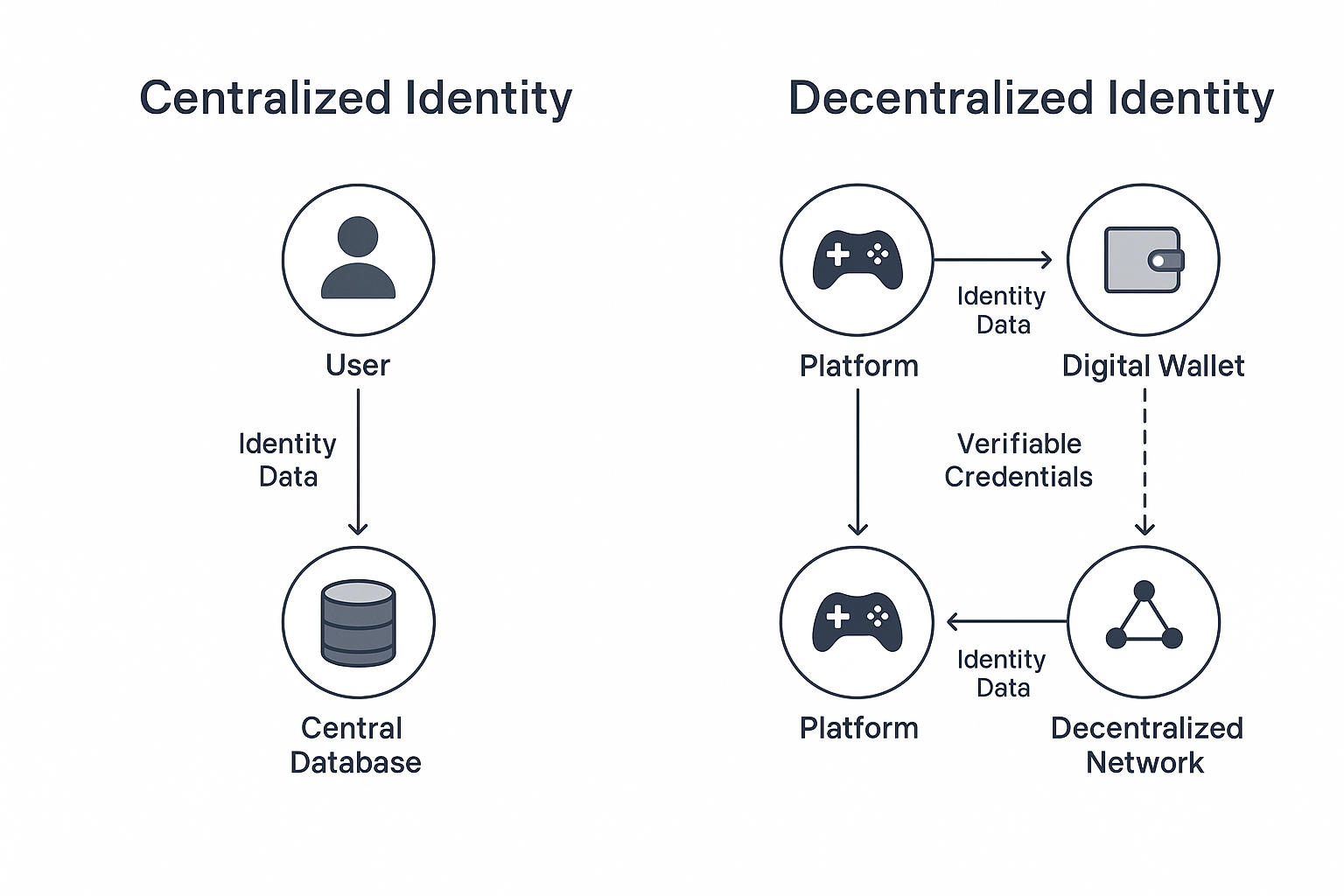
Decentralized identity (DID) provides an alternative approach to user authentication and data management. Unlike traditional centralized models, DID empowers users to control their digital identities using blockchain-based, verifiable credentials.
Here's why DID is a compelling solution for enhancing security in gaming:
- User Control and Privacy: DID allows users to store their credentials, often as verifiable credentials, in a secure digital wallet. Users can then selectively share only the necessary data with platforms, minimizing exposure and significantly enhancing privacy.
- Reduced Single Points of Failure: By distributing identity data and verification mechanisms across a decentralized network, DID eliminates reliance on a single central database, making large-scale data breaches significantly more difficult.
- Stronger Authentication: DID supports more robust authentication methods, including passwordless login and cryptographic proofs, which are less vulnerable to interception compared to SMS-based methods.
- Minimized Third-Party Risks: Decentralized systems reduce the dependency on potentially vulnerable third parties for core identity functions, mitigating supply-chain weaknesses.
- Interoperability: DID standards, such as those defined by the World Wide Web Consortium (W3C), promote interoperability, allowing users to potentially use a single, secure identity across different platforms, simplifying the user experience without compromising security.
For gaming platforms, adopting DID can enhance the security of millions of user accounts, build greater trust with their player base, and establish a higher standard for identity security in the industry.
ArcBlock: Leading the Charge in Decentralized Identity#
Among vendors in the DID space, ArcBlock offers a platform designed for secure identity management and decentralized application development. ArcBlock's ecosystem is built to support developers and businesses looking to implement decentralized solutions. Key aspects of ArcBlock's offering include:
- DID Wallet: A decentralized wallet designed to allow users to manage their digital identities and credentials, aiming to provide users with control over their data.
- W3C-Compliant DID: ArcBlock adheres to global DID standards, which is essential for potential interoperability and integration with other standards-based systems.
- DID Connect: A toolkit intended to help developers build custom DID applications and integrate decentralized identity features into their platforms.
- Scalable Architecture: ArcBlock's underlying blocklet and blockchain infrastructure is designed with scalability in mind, aiming to handle a large volume of transactions and users, which is a necessary feature for platforms like Steam.
- Privacy Features: The platform incorporates features like selective disclosure and zero-knowledge proofs, designed to protect user data and support compliance with privacy regulations.
ArcBlock's focus on providing a comprehensive platform and developer tools positions them as a potential partner for enterprises and governments exploring decentralized identity solutions.
Key Differentiators of ArcBlock's DID Capabilities#
Feature | ArcBlock Advantage |
|---|---|
W3C-Compliant DID & Verifiable Credentials | Built to global standards for maximum interoperability |
DID Connect Toolkit | Enables developers to quickly integrate decentralized identity features |
Blocklet Infrastructure | Modular and scalable architecture supports millions of users |
Privacy by Design | Supports selective disclosure and zero-knowledge proofs |
Multi-Chain Ready | Operates across different blockchain ecosystems |
Potential Action Plan: Exploring Decentralized Identity#
For platforms like Steam, or gaming companies, considering the adoption of DIDs, a phased approach using technology like ArcBlock's could involve the following steps. Note that these timeframes are estimates and the actual duration could vary significantly based on integration complexity, testing requirements, and resource allocation.
- Assess Current Identity Systems
- Objective: Identify existing vulnerabilities and evaluate the feasibility of integrating decentralized identity.
- Actions: Conduct a thorough audit of current authentication methods, data storage practices, and dependencies on third-party identity services. Map out potential points of failure.
- Outcome: A detailed report outlining security gaps and identifying specific opportunities for DID implementation.
- Pilot a DID Solution
- Objective: Test decentralized authentication with a limited user group to test for bugs and usability.
- Actions: Partner with a vendor like ArcBlock to Implement its DID-based solutions including authentication (e.g., passwordless login or cryptographic 2FA) for a subset of users (e.g., 10,000 to 100,000). Assess compatibility with existing infrastructure or other ArcBlock systems needed to meet requirements.
- Outcome: A working pilot demonstrating the technical viability and user experience of DID authentication.
- Plan for Integration and User Adoption
- Objective: Develop a comprehensive strategy for integrating DIDs across the platform and how to educate users.
- Actions: Approve architecture and plan user education campaigns to highlight the benefits of DID (enhanced security, privacy, control). Prepare developer resources and training for internal teams.
- Outcome: A detailed rollout plan and educational materials for users and developers.
- Phased Implementation and Scaling
- Objective: Gradually roll out DIDs across the entire user base and integrate it into core platform functions.
- Actions: Begin phased deployment of DID authentication, potentially starting with new users or as an enhanced security option for existing users. Integrate DID into login, account management, and other relevant systems. Scale the underlying infrastructure to handle the platform's user base.
- Outcome: A successfully integrated, secure, and user-centric decentralized identity system for the platform's global users.
- Monitor and Iterate
- Objective: Continuously monitor system performance, security, and user feedback for ongoing optimization.
- Actions: Utilize monitoring tools to track the performance and security of the DID system. Collect user feedback to identify areas for improvement. Address technical issues and user concerns promptly.
- Outcome: A continuously improving and resilient identity system.
Expected Benefits#
By exploring and potentially implementing DID, platforms can aim to achieve:
- Enhanced Security: Reduce reliance on centralized systems and vulnerable third parties, mitigating the risk of large-scale breaches.
- Increased User Trust and Control: Empower users with greater control over their identity data, fostering trust and aligning with growing privacy expectations.
- Potential for Industry Leadership: Set a precedent for secure and privacy-preserving identity management in the gaming sector.
- Improved Scalability and Resilience: Leverage the distributed nature of blockchain and DID for a more robust and scalable identity infrastructure.
Visit www.arcblock.io to learn more about decentralized identity or to get more information about how DIDs can help your company.
Conclusion#
The alleged data leak linked to a third-party service used by a major gaming platform serves as a reminder of the inherent risks in centralized identity systems. Decentralized identity, with its focus on user control, reduced reliance on central authorities, and enhanced security features, offers a promising path forward. ArcBlock's platform is designed to enable companies of all sizes to adopt DID. While the transition does require planning and execution, exploring and implementing decentralized identity solutions presents an opportunity for gaming platforms to significantly enhance security, protect user data, and build a more trusted digital environment for their millions of players.
