Recently, cybersecurity researchers exposed a 47GB database containing over 184 million passwords and login credentials. Accounts from tech giants—Google, Microsoft, Facebook, Apple—and even government email domains from 29 countries were all caught in the net. It’s another headline, another wake-up call, and another reminder: centralized identity systems are broken.
What Actually Happened?#
A third-party threat intelligence firm stumbled on an exposed database that wasn’t protected or even encrypted. Anyone with the link could access user credentials—email addresses, passwords, and more—most harvested through malware and infostealers, then dumped in a single, easy-to-download location. This data is now circulating on dark web forums, waiting to be exploited for phishing, fraud, and identity theft.
The Core Problem: Centralized Identity#
Most online services still rely on a single point of failure: usernames and passwords stored in central databases. If an attacker gets in (and they do, regularly), everything is exposed—at scale.
- Centralized databases are high-value targets.
- Passwords are reused across sites, compounding risk.
- Users have no control over what happens to their credentials.
No amount of “strong password” advice can fix a fundamentally broken architecture.
The Decentralized Identity (DID) Alternative#
Decentralized identity flips the script. Here’s what it is, and why it works:
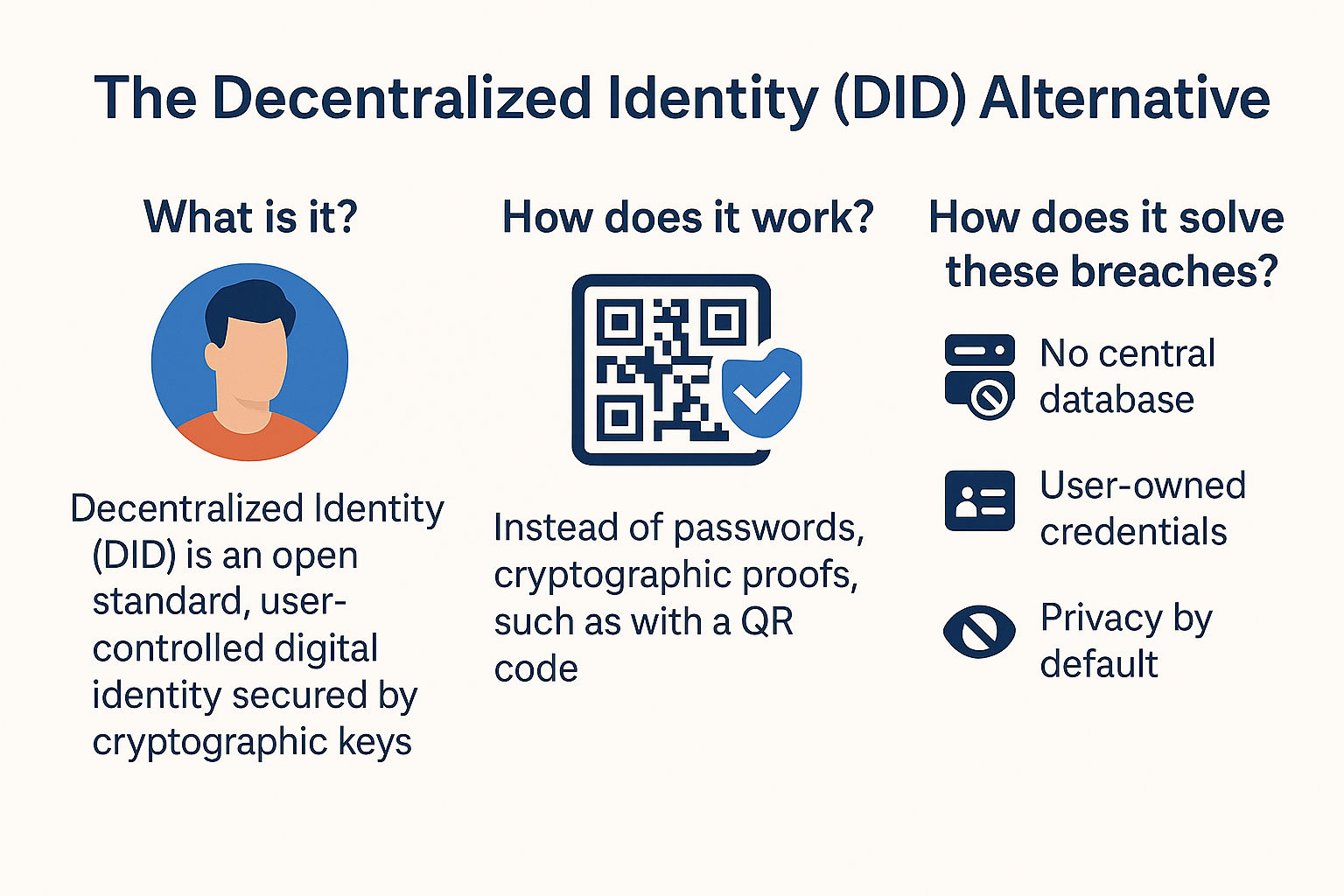
- What is it?
Decentralized Identity (DID) is an open standard for managing digital identity that does not rely on any single provider or database. Each user owns a digital identity that only they control, secured by cryptographic keys on their own device or wallet. - How does it work?
Instead of giving out passwords to dozens of sites, a user proves their identity using cryptographic proofs—often with a QR code or wallet signature. No passwords are stored, and no personal data is sitting on a server waiting to be breached. - How does it solve these breaches?
- No central database to hack.
Attackers can’t compromise millions of users at once—there’s simply no target. - User-owned credentials.
Even if a business is breached, no reusable secrets are exposed. - Privacy by default.
Users share only what’s necessary—no mass data collection.
- No central database to hack.
ArcBlock: Making Decentralized Identity Real for Businesses#
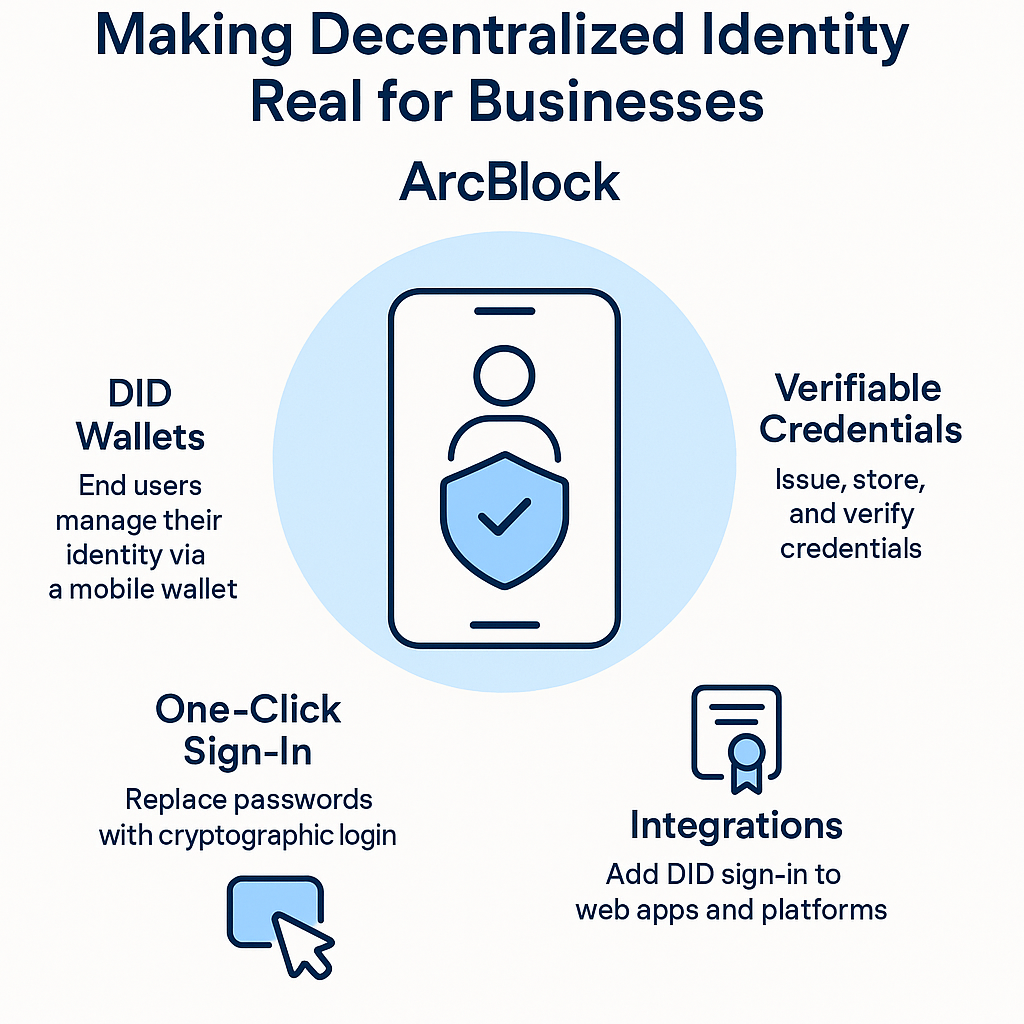
ArcBlock’s DID platform lets any business build secure, user-friendly decentralized identity into their products—without having to be a cryptography expert.
Capabilities:
- DID Wallets: End users manage their identity via a mobile wallet, not a centralized database.
- One-Click Sign-In: Replace passwords with cryptographic login—faster and more secure.
- Verifiable Credentials: Issue, store, and verify credentials (like KYC, memberships, certificates) without the risk of data theft.
- Privacy & Compliance: No more mass data storage, easier compliance with privacy regulations (GDPR, CCPA).
- Integrations: Add DID sign-in to web apps, SaaS, and enterprise platforms with a few lines of code.
The Bottom Line#
As long as the world runs on passwords and centralized accounts, breaches like this will keep happening. App builders, businesses and dev teams have a choice: keep patching a broken system, or lead the shift to decentralized identity.
ArcBlock has already enabled leading companies to build and deploy decentralized identity solutions, making these headlines avoidable—not inevitable.
If your company is still storing passwords, you’re playing with fire. It’s time to switch to decentralized identity—and put your users back in control. Learn more at www.arcblock.io
